Phishing at The U: Scam to Look Out For!
Learn how to protect yourself from phishing!

Identity fraud is becoming an increasingly critical issue for consumers and businesses alike. One of the ways hackers are able to steal personal data and commit identity fraud is through phishing, a type of cyber-attack through email with the goal of tricking the recipient into sharing personal information, such as passwords or banking information, which can be used to commit various types of fraud.
The issue is growing at an alarming rate, as more personal information is available on social media channels and websites, and hackers are able to craft targeted phishing emails that are personalized for the recipient, which are more likely to bypass organizational and personal security checks and systems.
At the U, we use a variety of measures to protect email, including advanced threat protection tools. However, scammers are constantly changing tactics. Being aware of phishing schemes and understanding email best practices can help ensure your email stays safe.
Recent Scam Attempt at the U
Over the past few months, Universities have seen a spike in the "Are You Available?" scam. It looks something like this:
You just received a message from a very important person at the University. Possibly a dean or an executive leader. The senders email address may include the first and/or last name of the person, but will be from a non-miami.edu destination like Gmail or AOL. The subject line reads "hello," "urgent request," or "are you available?"
Because it seems urgent, you open the message to read a simple one or two line request: "Are you available right now?"
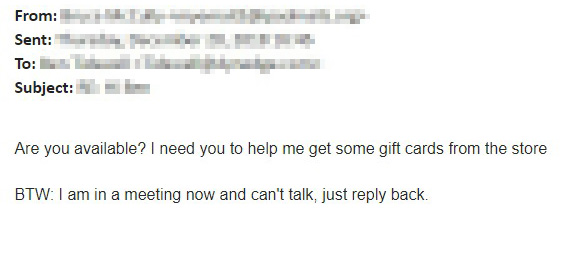
If you respond to that first email, the scammer writes back immediately saying something like: "I'm busy in a meeting where phones can't be used, need your help right away. Can you quickly get me gift cards and send the digital numbers to this email address. I'll reimburse you when I get back to the office."
There are other variations of this scam; see below for one recent example:
How to Prevent Phishing Attacks from Happening to You
- Think before you click. If it seems suspicious, take a moment to hover over the links and inspect details within the message, like the sender’s email address, to ensure it's a trusted sender.
- Always check the spelling of the URLs in email links and/or the URL bar before you click or enter sensitive information.
- Watch out for URL redirects, where you're subtly sent to a different website with identical design.
- Check the domain of the sender. If it’s not miami.edu, verify the sender’s authenticity before replying.
- If you receive an email containing the name of someone you know, but it seems suspicious, contact that person directly with a new email or a phone call, rather than just replying.
- Do not post personal data, like your birthday, vacation plans, or your address or phone number, publicly on social media.
- In the event that you fall victim to a phishing scam, please contact the IT Service Desk at IT Service Desk and the IT Security team at infosec@miami.edu.
Learn More About Phishing
What is Phishing?
Phishing is a form of fraud in which an attacker sends an email masquerading as a reputable person or company to attempt to learn private information. Phishing scams trick people into sharing user IDs and passwords, downloading infected files, or clicking bad links, which can lead to identity theft.
The end result of successful phishing attempts differs from one scam to the next. The most common types of attack result in a hacker gaining access to sensitive information (like the password to your online banking site or your email account), access to the information you store on your laptop or mobile device, or even control of your device.
Take a look at the following statistics, which show that phishing is truly a large-scale and worldwide issue:
- Phishing accounts for 90% of data breaches (Verizon)
- The average financial cost of a data breach is $3.86 million (IBM)
- Business email compromise (BEC) scams accounted for over $12 billion in losses (FBI)
- 76% of businesses reported being a victim of a phishing attack in the last year (Wombat Security)
- 30% of phishing messages get opened by targeted users (Verizon)
- Around 1.5 million new phishing sites are created each month (Webroot)
- In a survey of over 1,300 IT decision makers, 56% of organizations identified targeted phishing attacks as their biggest current cyber security threat. (CyberArk)
For more information, and samples of these scams, please read UMIT's "Don't Get Phished: Protect Yourself and Stop Identity Theft" article. To learn more about phishing and learn how keep your identity safe, please download UMIT's Phishing 101: How to Spot a Phishing Attempt and Phishing 101: Tips to Protect Yourself documents.
If you suspect a message to be a phishing attempt, you can quickly report it using Outlook's "Report Phish" feature. If you are not using Outlook or the feature is not available, you can forward the phishing email (as an attachment) to phish@miami.edu.
If you are victim of phishing, e.g., you clicked a link and/or downloaded an attachment from a suspicious source, please contact the IT Service Desk at IT Service Desk and the IT Security team at infosec@miami.edu.





