#1
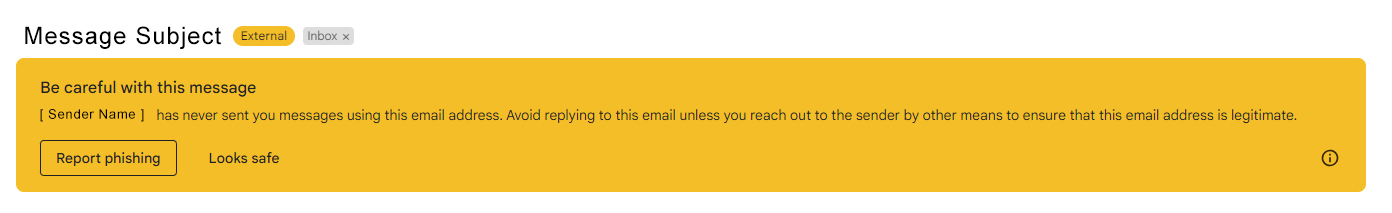
Do not trust the display name of who the email is from.
Just because the email says it is coming from a name of a person you know or trust does not mean that it truly is. Be sure to look at the email address to confirm the true email sender.
Phishing (pronounced "fishing") is a form of fraud, in which an attacker tries to learn private information (such as login credentials) by masquerading as a reputable entity or person (usually via email). The University community should remain on high alert for suspicious emails or activity that may compromise our organizational data or employee information.

Additionally, as our first line of defense against cybercriminals, all University of Miami community members are encouraged to watch for these 10 things when it comes to detecting phishing emails:
Do not trust the display name of who the email is from.
Just because the email says it is coming from a name of a person you know or trust does not mean that it truly is. Be sure to look at the email address to confirm the true email sender.
Look but do not click.
Hover or mouse over parts of the email without clicking on anything. If the text looks strange or does not match what the link description says, do not click on it—instead, report it to phish@miami.edu.
Check for spelling errors.
Attackers are often less concerned about spelling or being grammatically correct than a normal sender would be.
Consider the salutation.
Is the address general or vague? Is the salutation to "Valued Customer" or "Dear [Insert Title Here]"?
Is the email asking for personal information?
Legitimate organizations are highly unlikely to ask for personal information in an email.
Beware of urgency.
These emails might try to make it sound as if there is some sort of emergency. A common example is that someone only needs $100 so they can claim their million-dollar reward.
Check the email signature.
Most legitimate senders will include a full signature block at the bottom of their emails.
Be careful with attachments.
Attackers like to trick you with an enticing attachment name. It might have a long name, or it might be a fake Microsoft Excel icon that is not actually the spreadsheet it claims to be.
Do not believe everything you see.
If something seems slightly out of the norm, it is better to be safe than sorry. If you see something off, it is best to report is to the IT Service Desk.
When in doubt, contact the IT Service Desk.
No matter the time of day, the IT Service Desk encourages you to report something of concern.
Copyright: 2025 University of Miami. All Rights Reserved.
Emergency Information
Privacy Statement & Legal Notices
Individuals with disabilities who experience any technology-based barriers accessing University websites can submit details to our online form.